Audit M2M Access
Machine-to-Machine Access to Organizations can be granted by directly associating a client grant to an organization or allowing access to any organization in the client grant settings. Both scenarios can be audited via the Auth0 Dashboard or the Management API, where you can view or retrieve a list of client grants associated with an organization for an application. To learn more about how M2M access to Organizations permissions work, read Configure Your Application for M2M Access and Authorize M2M Access.
Access granted via direct association
Use the Auth0 Dashboard and Management API to audit M2M access for client grants that are directly associated to an organization.
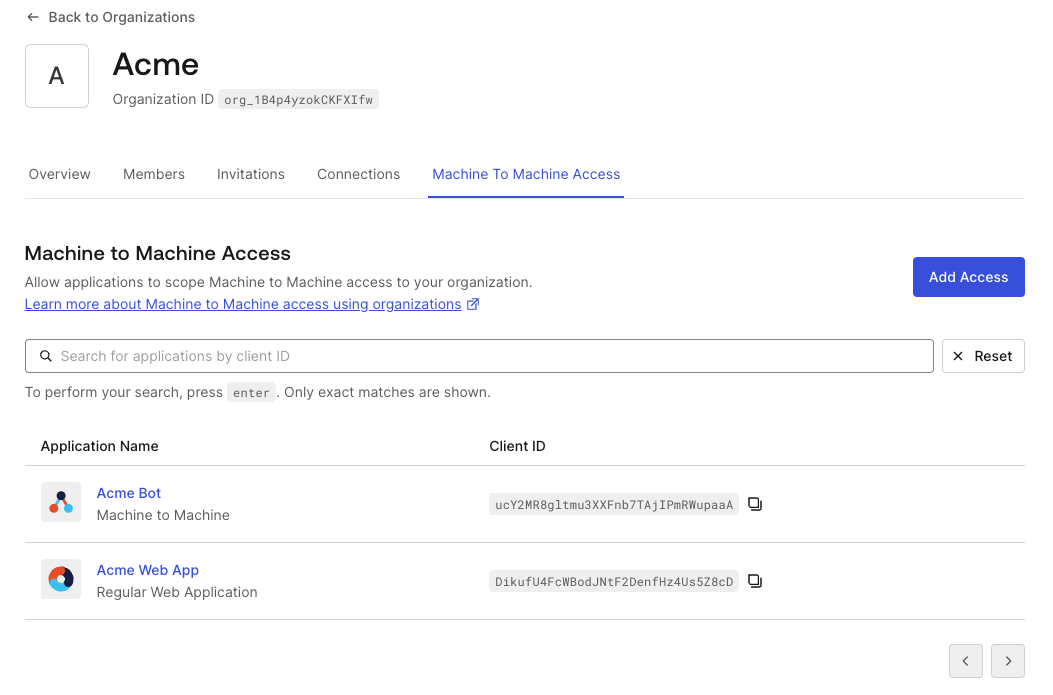
To view the application client grants that have been authorized for a specific organization on the Auth0 Dashboard:
Navigate to Organizations and choose the organization you wish to inspect.
Select the Machine-to-Machine Access tab. You will get a paginated list of all the applications that can access an API for this organization via direct association.
Choose an application to review the authorized APIs listed for that application.
Client grants associated with an organization can be retrieved via the Organization Client Grants API endpoint:
curl -X GET --location "https://{YOUR_DOMAIN}/api/v2/organizations/{ORG_id}/client-grants/" \
--header 'authorization: Bearer MGMT_API_ACCESS_TOKEN'Was this helpful?
Alternatively, if you want to retrieve information on applications that can access at least one of the API for an organization, you can use the q query parameter on the Get Clients API endpoint with the search term client_grant.organization_id:{organization_id}. Use the Lucene syntax, which is similar to the User Search Query Syntax.
curl -X GET --location "https://{YOUR_DOMAIN}/api/v2/clients?q=client_grant.organization_id%3Aorganization_id" \
--header 'authorization: Bearer MGMT_API_ACCESS_TOKEN'Was this helpful?
Access granted to any organization
Use the Auth0 Dashboard and Management API to audit M2M access for applications that have access granted to any organization.
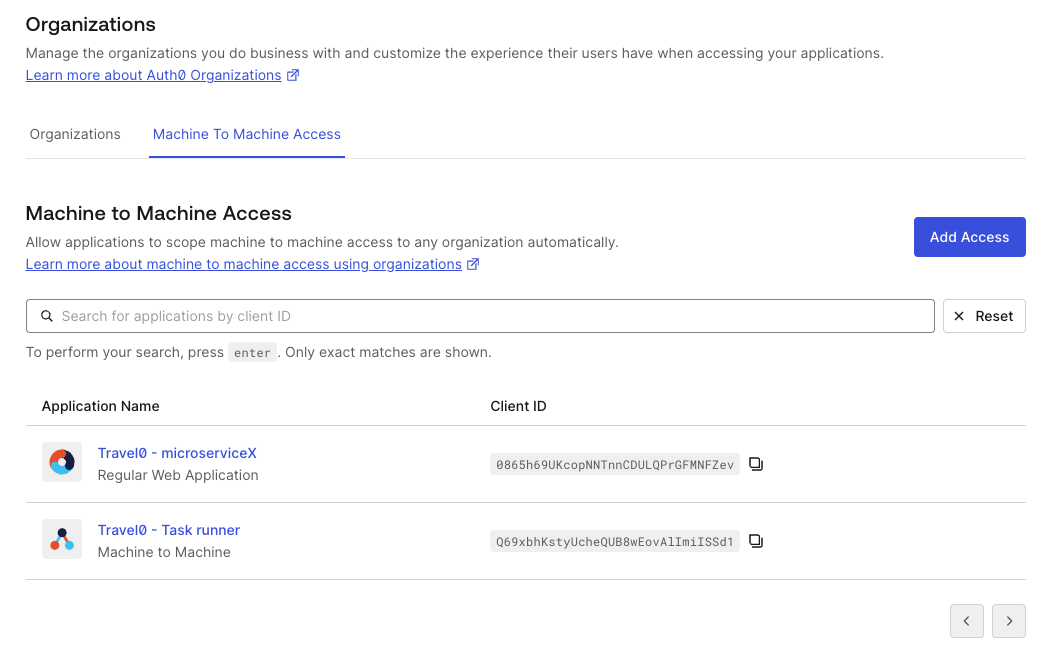
Navigate to Organizations.
Select the Machine to Machine Access tab. You will get a paginated list of all the applications that can access at least one of the API for an organization.
Choose an application to review the authorized APIs listed for that application.
Client grants with the allow_any_organization parameter can be retrieved via the Get Client Grants API endpoint:
curl -X GET --location "https://{YOUR_DOMAIN}/api/v2/client-grants?allow_any_organization=true" \
--header 'authorization: Bearer MGMT_API_ACCESS_TOKEN'Was this helpful?
Alternatively, if you want to retrieve information on applications that can access at least one of the APIs for any organization, you can use the q query parameter on the Get Client Grants API endpoint with the search term client_grant.allow_any_organization:true. Use the Lucene syntax, which is similar to the User Search Query Syntax.
curl -X GET --location "https://{YOUR_DOMAIN}/api/v2/clients?q=client_grant.allow_any_organization%3Atrue" \
--header 'authorization: Bearer MGMT_API_ACCESS_TOKEN'Was this helpful?
Search applications based on organization access
The following table shows the search terms supported to query applications with the q parameter on the /clients endpoint:
| Field | Description |
|---|---|
client_grant.organization_id:{organization_id} |
Use to search for applications that can access at least one of the APIs for an organization. |
client_grant.allow_any_organization:true |
Use to search for applications that can access at least one of the APIs for any organization. |
Tenant logs
Machine-to-Machine Access for Organizations is also reflected in tenant logs. You can check the organization associated to the request in the corresponding seccft tenant log.
The following code sample is an example seccft tenant log with organization information:
{
"date": "2024-10-24T19:06:17.460Z",
"type": "seccft",
"description": "Client Credentials for Access Token",
"connection_id": "",
"client_id": "qoQKtXuhdSibs1jUeXk3mmCwXoAafGnO",
"client_name": "jwt.io (Test Application)",
"ip": "130.41.219.72",
"user_agent": "Other 0.0.0 / Other 0.0.0",
"hostname": "david-test.test-aws-abundant-lobster-6004.auth0c.com",
"user_id": "",
"user_name": "",
"organization_id": "org_mPdwToiiHHOtz0SH",
"organization_name": "cc_test",
"audience": "https://jwt.io.com",
"scope": "read:data",
"$event_schema": {
"version": "1.0.0"
},
"log_id": "90020241024190617517817000000000000001223372036854775862",
"tenant_name": "david-test",
"_id": "90020241024190617517817000000000000001223372036854775862",
"isMobile": false,
"id": "90020241024190617517817000000000000001223372036854775862"
}Was this helpful?